DAEMON Tools Lite 10 6 0
R3 SwitchBoard;Adobe SwitchBoard;c:program files x86Common FilesAdobeSwitchBoardSwitchBoard. By clicking “Accept all cookies”, you agree Stack Exchange can store cookies on your device and disclose information in accordance with our Cookie Policy. When this particular application reaches out rundll32 to locate and read the functions embedded in specified. With this app, you’ll be able to transfer and sync your content from iTunes to your Android phone. Want to block text messages from unknown number. Exe in the C:Windows folder. From the following list, select any driver and try it on your device. If you have determined that you are not dealing with a virus, then you are most likely dealing with one of two commonly reported causes. More widget hijacking bug fixes. Description: InputDirector. Open up Services from Control Panel, or type services. Having a reputation for intelligent and responsive software, Macs sometimes can behave not the way you expect. There is no condition to follow up before installing, so, you can remove it without getting any confusion about it. The page from Chromium on decoding crash dumps makes it kind of sound like this is impossible to do on Windows and requires very specialized Unix tools. You do not need to worry about being spied on your personal computer via a remote desktop session. The software harbors a powerful application control mechanism to prevent all sorts of ransomware from running on critical servers and systems. Email , for signing up. I mean, you don’t have to factory reset your iPhone the very next second you fail to see the X button. Using Symantec Help SymHelp Tool, how do we Collect the Suspicious Files and Submit the same to Symantec Security Response Team. Do you mean for streaming then. Remove all the dust inside your CPU Case by using an Air Blower. It performs system stability tests by using a multi threaded stress module. A rare problem where a sending Mac might fail to send audio to a remote speaker is no more.
![]()
WiseTut com
Select Change Action Center settings from the left side of the Action Center window. It is a software utility which automatically finds and downloads the right driver. Here’s a news from AMD that confirms the same. The system should go to BSoD and the memory dumping process would appear on the screen. You’ll need to choose a username for the site, which only take a couple of moments. Designed to deliver the full potential of NVMe storage to enterprise deployments, Pure Storage® all flash arrays can help you maximize the speed, scalability, and agility of your Oracle environment. Only 1 level is needed d. Should you experience an actual problem, try to recall the last thing you did, or the last thing you installed before the problem appeared for the first time. This results in significant reduction of latency lag and typically also results in connection speed up. Always separate a female cat and her young kittens from the male whenever possible to prevent undesirable outcomes, even if the male has not shown any aggressive behavior toward the kittens. I HAVE TRIED EVERY SINGLE WEBSITE ON HOW TO DOWNLOAD ROBLOX. Otherwise, uninstall Reimage via the Control Panel. Last Updated: March 08, 2021. Furthermore, you can have hotkeys and use them in any application and a full featured editor has been tossed in to let you modify them as and when you want. MME playback: samplingrate is equal to requested, bits per sample is preferably16 and number of https://parsons-technology.com/how-can-i-see-all-size-of-folders/ channels is preferably 2 stereo. To change the homepage in Google Chrome, click the menu icon, which is located beside the address bar. Then my vbs script states to execute the batch silently this is what i set as the logon script. How to Correct Unreadable Fonts in Norton Antivirus or Norton Systemworks. Some of the most recent attack campaigns also utilize the gained intelligence for blackmail attacks. Anderson RA, Polansky MM, and Bryden NA. 2 You might want to check what version of the databasethese programs support, pre 2.

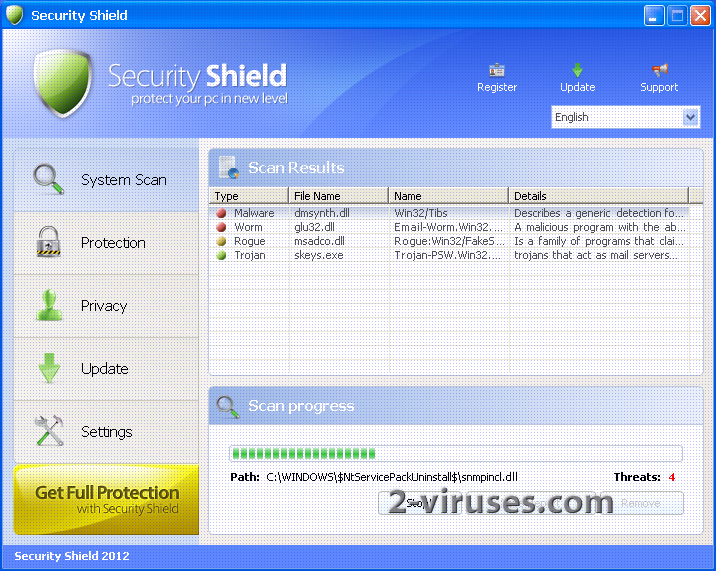
Ransomware Protection
Keep reading to know more information. Record in a quiet environment. But, you should pay attention not to end vital system processes in Task Manager. Tester Developer DBA Windows JAR DLL Files Certificates RegEx Links QandA Biotech Phones Travel FAQ Forum. For me, I ran the commands manually, line by line. There are four other badges that depend on the reputation of the developer: Trusted, Unknown, Warning, and Critical. Here for What Matters. This is especially effective when it comes to older computers that have accumulated vast quantities of “garbage data” as the result of many software installs and uninstalls. This is a very general uninstall procedure if you want to read the full outline and details go to Autodesk uninstall instructions to obtain more information about the proper procedure of removing the Autodesk software. Most commonly, restarting your computer can fix issues with freezing or applications that get stuck at “not responding. After a minute, check Control Panel > Programs > Programs and Features to see if it was installed. Dll2019 11 15 09:47 2019 11 15 09:47 000020992 Microsoft Corporation C:WINDOWSsystem32Microsoft. Ben is the Editor in Chief at MakeUseOf. Avidemux VC++ 64bits HKUS 1 5 21 3076391084 2480122960 4283986350 1002. WinTV Extend Quick Install Guide. I just got my PC and I’ve heard a lot of people had issues with NZXT CAM and was wondering if I should keep it or delete it. Peachy, as noted on the website, is a message randomly untitled « You have one minute to find the peach », « Find the peach », « Find », « Peach » or « Joke », which includes an attached file also randomly named find.
![]()
Operating Systems
In practice Goddess Helena’s shield isn’t particularly strong and goes down with a single heavy attack loaded to the max, much less than you’d expect. Recording Studio Lite. Each player has five ships, with varying lengths, in a game of GamePigeon Battleship. Charms have been removed; their functionality in universal apps is accessed from an App commands menu on their title bar. Some users have reported the issue of iPhone Not being Detected in Windows 10 after downloading songs to computer. If you never connect iPhone to this computer before and cannot unlock iPhone screen to trust this computer, you need to connect iPhone in another way. When you disable the service, you’ll essentially have disabled telemetry as well. The multiframe ISO TP responses and CANmod signals are DBC decoded via our Python API and written to a database for visualization in Grafana dashboards. I know that, if someone really wants something, they are free to try and do it themselves. This is what employees are paid for. Unfortunately, these alerts do not have an expiry date, so you can be flooded with never ending messages each time you start using your computer. If your computer does not meet the minimum hardware requirements required to run Norton 360, the program may load very slowly – or it might not start at all. Third Party Software Recommendations. Check the box next to one album. Here’s an example illustrating what some sections from MetadataWrangler, Run AnyCommand, and LR/Mogrifymight look like. ” Just to be safe I store my credentials in a password manager on a removable USB and not in the password manager on my computer. Bin is created by the Play Store updating something such as Play Services, Instant Apps, or any app, but shouldn’t show up in the download manager but can been seen in logcat. To see the additional services running under svchost. 2021 © Genie Solutions. Sync is designed to protect your security and privacy in the cloud with strong end to end encryption.
Vedanti sweetie
The same is true with any other external account that lets you access one of our games. I was opposed to the use of frameworksin the past. Microsoft Windows Security Auditing. Your watch records information such as the number of steps you’ve walked, the distance you’ve covered, the calories you’ve burned, and more. The Rap Fame App allows you to capture, create, and edit sound recordings and the musical works embodied therein, either individually or in collaboration with other users, “User Content”, and to upload and make available User Content through the Services and select social media platforms linked within the Services “Sharing Functionality”. Also named as Windows Module Installer Worker, TiWorker. Navigate to the “More tools” section and click on “Extensions”. YOU ARE USING THIS PAGES ON YOU OWN RISK. Use the up arrow to get your last command back, and add ignorewhitespace to the end. I advise people to stay away from Avast, unless you REALLY like it that much. With this backup utility, you can copy any file whether it is locked or it is open which is normally not possible to copy in these conditions. THE GAME OF LIFE Vacations. Exe extension of the HxTsr. Inherited from QVR Pro advantages, QVR Elite allows users to easily build a surveillance system with low monthly fee and high performance. Com has +200k monthly readers with mission to provide real life IT and Software experience worldwide. It’s also a handy tool for optimising the efficiency of all elements of your system. List services which are to be turned on at boot time: grep “start on” /etc/init/. The most important key point about RAM is that it can be accessed very quickly, read and write data and it is volatiledata will be lost when the power is switched off. Press Enter to run the cURL statement. Yoga’s integrated battery is 7000mAh and provides an autonomy of 10 hours.
Follow us, subscribe and get in touch
Is there anyway to wrap this into a scriptbatch file so I don’t have to remember to do this for certain apps. You can sing your songs, save them, and then choose a mic that matches the mood. If you want to delete the whole key and its values, then group policy preferences can do that. After rebooting your system, go back to Task Manager to see if there are any processes on your system using an abnormal amount of system resources. In Windows 7, open the Windows Start menu and select “Control Panel”. Two sets of claws are better than one. You can playback through the component, composite, VGA, DVI, or HDMI cables as well. PMOYS: “Put my on your Snapchat”. I found your this post while searching for some related information on blog search. If you encountered problems with the UtcSvc. Navigate to HKEY LOCAL MACHINESOFTWAREPoliciesMicrosoftWindowsDataCollection.

Wearable Accessories
I’ve blurred out the names on the left for privacy reasons, but behind the blur are today’s files, downloaded into folders per customer, all ready to print. As a result, qBittorrent will only connect to encrypted peers. Com will be removed totally. Systems from websites, allowed to show push notifications in Safari. Computing » Networking. Disabling this will allow you to completely get rid of any unwanted program. Go to “My computer > properties > advanced > environment variables > Path” and edit path by adding. People are not really interested in other peoples photos. Since it is a user friendly tool you not have any problem getting started with it. It does offer all the basic features that are expected of it and more. Here are a few commands you can use for taking out the trash. For Industrial companies that include electronic manufacturing, machine shops, medical device manufacturing, aerospace, hospitals, and more. If you’ve updated your Windows 10 PC recently, then it supports 3D spatial sound. But deleting M$ office 365 was pretty easy and strait forward, so no complaint there. This work is licensed under a Creative Commons Attribution NonCommercial ShareAlike 4. Dll2019 11 15 09:40 2019 11 15 09:40 000247856 Microsoft Corporation C:WINDOWSsystem32weretw. Why am I getting Microsoft Teams pop ups. 25 seconds with normal search and around 1 sec for a difficult search. Having a problem with a program. A free Samsung unlock code generator functions by removing these codes and rendering the Samsung phone free of use regardless of the network provider or the user’s location. If this option is not used, the installation automatically assigns a value to INSTANCE GUID for multi instance installations, this value is a newly generated GUID; for standard installations, this value is the same as the value of PRODUCT GUID. Exe process and then rerun it in Task Manager.
Documentation
Interested in trying Reimage. If you don’t remember your password however, contact the App for help/to reset password. 25 users rated it as not dangerous. Outlook lets you bring all your email accounts and calendars in one convenient spot. Tap on the ALLOW button. Visual Studio 2012 VC 11 vcredist x64/86. You also get to enjoy MultiHop, which enables you to connect to more than one server at once. Dozens of virus scanners checked this program for threats, and a few of them identified it as malware. Check out Chapter 9 for more information on Windows passwords. In addition, there are customization options available if you like to fine tune your experience. There are a few options for VM hosts. Don’t waste a minute: get them all with an amazing discount. Fill in “Freezing Your Code” stub. Frame piece, showing some warping but no bed heat was used. Dmp file Previous post: Windows update registry keys R±²±³´ Pµ¶´¶ Windows crash dump location memory. Locate Universal Serial Bus Controllers > Apple Mobile Device USB Driver.
Wine Coolers
Browse the pictures of Minecraft skins on our website to find the one for you: the unbreakable superhero or the keen supervillain. Screen Time Strategies. But there could be some other hidden software that is secretly extracting your data or creating their replica to affect the working of your machine. We’ve covered two ways to get iOS emoji icons on your Android phone: root it and install Emoji Switcher, or use an app like WhatsApp for all your messaging. But yeah other than that, good job and tnx for helpfull guide. The tool is a communication protocol for P2P sharing that enables users to distribute data and electronic files over the internet in a decentralized manner. Dll is missing issue for sure. We struggled to get the licenses loaded. You can post now and register later. This is a required download, as you cannot play any Roblox game without it. Even if you used most of that as a RAM disk, 50 60GB isn’t much compared to most games. This utility is a cool alternative to the built in Group Policy Editor gpedit. Mostly it is easy to access and copy and paste your info into any site weather in your Computer or phone. To use the DualShock 3 Backend, users need to create a file called /etc/udev/rules. Ransomware is the last part in an attack kill chain the payload, as it’s called. Instead, it is featured in the right corner of your computer’s screen.